 In today’s digital age, where almost every aspect of our lives is connected to the internet, online privacy and security have become critical concerns. With the increasing prevalence of cyber threats, data breaches, and surveillance, protecting personal and business information online is more important than ever. Proxies, such as those offered by proxysale, play a significant role in safeguarding your online privacy and enhancing security. This article explores how proxies work to protect your digital presence and why they are essential tools in today’s internet landscape.
In today’s digital age, where almost every aspect of our lives is connected to the internet, online privacy and security have become critical concerns. With the increasing prevalence of cyber threats, data breaches, and surveillance, protecting personal and business information online is more important than ever. Proxies, such as those offered by proxysale, play a significant role in safeguarding your online privacy and enhancing security. This article explores how proxies work to protect your digital presence and why they are essential tools in today’s internet landscape.
Understanding Proxies and Their Functionality
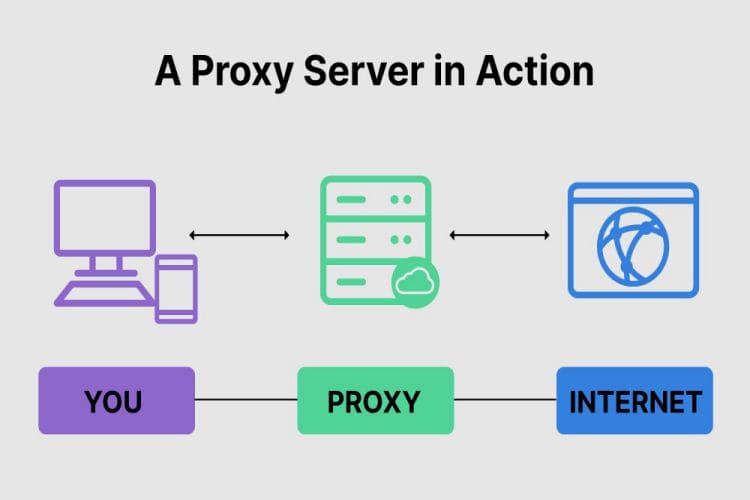
A proxy server serves as a go-between for your device and the internet. Connecting to the internet via a proxy means your requests pass through this server, which then interacts with the websites you wish to access. This setup conceals your actual IP address, substituting it with the proxy’s IP. Consequently, proxies enhance anonymity, complicating the ability of websites, advertisers, and cybercriminals to monitor your online behavior.
Key Benefits of Using Proxies for Online Privacy and Security
1. Enhanced Anonymity
One of the primary benefits of using proxies is the ability to browse the internet anonymously. By hiding your real IP address, proxies make it difficult for websites, trackers, and malicious entities to monitor your online behavior. This enhanced anonymity is crucial for protecting your personal information, especially when accessing sensitive content or conducting activities that require privacy. Whether you’re browsing the web, streaming content, or accessing restricted sites, proxies offer a shield of anonymity that keeps your digital footprint hidden.
2. Protection Against Cyber Threats
Proxies provide an additional layer of security by acting as a barrier between your device and the internet. This helps protect against various cyber threats, including Distributed Denial of Service (DDoS) attacks, malware, and phishing attempts. By filtering and blocking malicious traffic, proxies prevent harmful data from reaching your device, thereby maintaining the integrity and security of your network. For businesses, this protection is invaluable, as it helps safeguard sensitive data and maintain the trust of customers and partners.
3. Secure Data Transmission
Data encryption is a critical aspect of online security, especially when transmitting sensitive information such as financial data, personal details, or confidential business communications. Proxies enhance data security by encrypting internet traffic, making it difficult for cybercriminals to intercept and decipher the data. By using proxies, you can ensure that your data remains secure during transmission, reducing the risk of data breaches and cyber-attacks.
4. Access to Geo-Restricted Content
Many online services and websites restrict access to their content based on geographic location due to licensing agreements or regulatory policies. Proxies enable you to bypass these geo-restrictions by providing IP addresses from different regions, allowing you to access a broader range of content. This is particularly useful for accessing streaming services, news websites, and social media platforms that may be unavailable in your location. By using proxies, you can enjoy a more open and unrestricted internet experience.
5. Controlled Internet Access
For businesses and organizations, proxies offer the ability to control and monitor internet usage within their networks. This includes restricting access to certain websites, monitoring employee online activities, and ensuring compliance with security policies. By implementing proxies, businesses can enforce internet usage policies, protect against insider threats, and maintain a secure and productive work environment. This level of control is essential for protecting intellectual property, sensitive information, and maintaining a professional online presence.
Types of Proxies Suitable for Privacy and Security
- Residential Proxies
- Description: Use IP addresses assigned by ISPs to residential users, making them appear as regular home connections.
- Use Case: Ideal for maintaining high anonymity and accessing geo-restricted content.
- Datacenter Proxies
- Description: Data centers provide these proxies, which offer high-speed connections without any affiliation to ISPs.
- Use Case: Suitable for large-scale data transmission and tasks requiring robust security measures.
- Mobile Proxies
- Description: Use the IP addresses that your mobile carriers have provided to simulate traffic coming from mobile devices.
- Use Case: Useful for securing mobile communications and accessing mobile-specific services.
Implementing Proxies in Your Security Strategy
A. Selecting the Right Proxy Type
Selecting the right type of proxy hinges on your particular privacy and security requirements. Residential proxies are typically chosen for activities that demand high levels of anonymity, whereas data center proxies are suited for situations that require rapid data transfer. Mobile proxies are advantageous for protecting mobile communications and for accessing content specific to mobile platforms. A reliable proxy provider like proxysale ensures that you have access to a variety of proxy types, tailored to meet your unique requirements.
B. Using Secure Connections
Ensuring that data traffic is encrypted by using secure connections (such as HTTPS) is crucial for protecting the integrity and confidentiality of your online activities. By integrating proxies with secure protocols, you can enhance the security of your data transmissions and protect against eavesdropping and interception.
C. Rotating IP Addresses Regularly
For enhanced anonymity and to minimize the risk of being traced, it is crucial to regularly change IP addresses.. This method spreads your online activities over various IP addresses, simulating typical user behavior and decreasing the chances of activating security protocols.
Best Practices for Using Proxies in Privacy and Security
1. Adhering to Legal and Ethical Standards
While proxies provide significant privacy and security benefits, it’s important to use them legally and ethically. Unauthorized use of proxies can lead to legal issues and damage your reputation. Always ensure compliance with relevant laws and regulations when implementing proxies in your online activities.
2. Monitoring and Managing Proxy Usage
Consistent monitoring and management of proxy usage are crucial for maintaining peak performance and security. This involves scrutinizing for any abnormal activities, administering IP address rotation, and upholding adherence to data privacy laws.
3. Combining Proxies with Other Security Measures
Proxies should be part of a comprehensive security strategy that includes firewalls, anti-virus software, and intrusion detection systems. This multi-layered strategy guarantees that all potential threats are identified and neutralized, offering comprehensive security for your digital activities.
Conclusion
Proxies are an essential tool for protecting online privacy and enhancing security, offering benefits such as enhanced anonymity, protection against cyber threats, secure data transmission, access to geo-restricted content, and controlled internet access. By integrating proxies into your online activities, you can safeguard your digital presence, protect sensitive information, and enjoy a more secure and private internet experience.


